Web push scam: How to recognize and protect yourself online
 Aleksandra Kozioł
Aleksandra Kozioł
In general, web push is a versatile and effective form of communication with your customers and users. However, there is always a risk that someone will try and use push notifications to hack into your computer, steal your personal or financial data, or harm you in any other way. That’s why everyone, both companies sending push notifications and people receiving them should be aware of potential threats. And that’s what we want to discuss today.
Nowadays, cybercriminals are increasingly using push notifications as the initial vector for further attacks. Malicious pushes often use social engineering to strike fear into the victim (e.g., a push notification telling of a malware infection on a computer), and another expected response is to induce trust (an example would be a push notification from a seemingly familiar site - seemingly because we can recognize the logo of the company, however, everything else is specially prepared by the attacker). You can read more about sociotechnics in the new article from the CyberLabs series.
In recent weeks we could observe two types of malicious campaigns using push notifications:
notifications aimed at phishing, for example, for payment data (online skimmer),
notifications aimed at convincing the user to download and run malware.
In both cases, everything can start with malvertising (using advertisements to spread malware) or with PDF files injected into malicious sites in which we can find the so-called "fake captcha" after clicking which we are redirected to subsequent pages. During this we are asked to agree to push notifications. After giving our consent, we will start receiving scam notifications. At this point, depending on the cybercriminal's assumptions, we may be redirected to sites with fake stores where we can buy something at a big discount (in reality, it's a site with a so-called online skimmer that aims to defraud our payment card data).
The second scenario can look very similar to the previous one, however, in this case the push notifications impersonate, for example, Windows Defender and inform the victim that the computer is supposedly infected. By forcing on us the fear of losing e.g. data, we are forced to download e.g. a fake Windows Defender update which is supposed to get rid of the malware. In reality, we download malware which, once installed, will start stealing data from our computer.
Some time ago, McAfee, a cybersecurity solutions provider, shared information about fake push notifications informing that the user’s license has expired. Here’s how they looked:
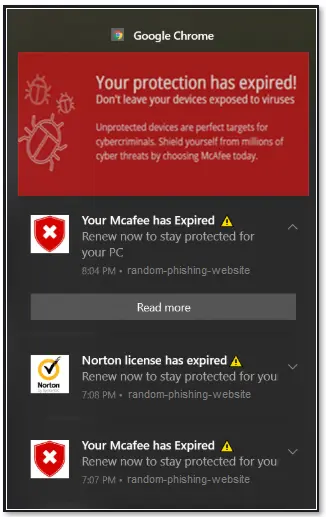
Source: https://www.mcafee.com/support/?locale=en-US&articleId=TS102999&page=shell&shell=article-view
For an untrained eye, such a notification can seem legit. However, when a user clicks it, they are not directed to the McAfee website but to a completely different place online where they can be attacked by a virus.
Such a notification can be displayed in the Notification Center like any other web push notification and, at first glance, it may look very similar to a system notification. That’s also very dangerous because many users will think it’s a recommendation from Microsoft. Take a look at this example:
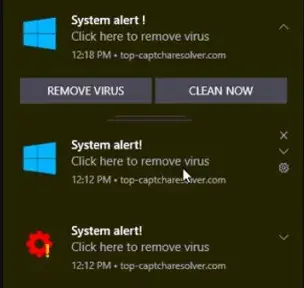
Source: https://news.trendmicro.com/2021/09/14/scam-alert-browser-notification-scams/
It’s all very convincing – the Windows logo, the “System alert!” message, and two buttons showing seemingly reasonable things to do – of course, you want to remove the virus and clean your computer, right? Unfortunately, once you click it, the opposite will happen, and your device will immediately be infected.
This raises a valid question – how can you recognize and protect yourself from malicious web push?
How to protect yourself from web push scam
It all starts with awareness. You have to be aware that web push, just like any other communication method, can be used to harm your data or your computer.

“I believe that with the growing interest in push notifications, there will also be an increase in the number of malicious notifications used by cybercriminals to spread malware or to target fake shopping sites that are integrated with so-called Skimmers. This is the inevitable future, so it is important to publicize this topic to build greater awareness among various people. Additionally, it is worth remembering about regular penetration testing of our systems so that the spread of malicious pushes does not start from our systems.”
Michał Błaszczak
Pentester @ Vercom S.A.
Here’s what you can do to protect yourself:
ANALYZE EACH PUSH NOTIFICATION BEFORE YOU CLICK IT
Before you click the button, take a thorough look at the notification. Does it refer to a website or app that you know and have been using in the past? Does it contain a correct URL address (there always has to be one)? Does it require you to do something that seems ok? Or maybe the action you’re asked to do seems weird or suspicious?
If there is anything that raises your concerns, don’t click or interact with such notification in any way!
Malicious web push usually emphasizes that you are in danger, you’re late with some payments, you have a debt, or someone is trying to hack your computer. Such a message has but one purpose – to scare you and encourage you to take immediate action. That seems reasonable – there’s something wrong, so you want to act quickly. Don’t do that. In nine out of ten cases, that’s someone trying to steal your data or hack into your device. Be extra careful with any dramatic or pressing messages, especially if they refer to financial questions.
ACCEPT PUSH NOTIFICATIONS KNOWINGLY
Web pushes will never show on your device if you don’t let them first. And to do that, you have to click consent to receive them. Never give permission if you’re on a website you’re unsure of. It’s safer to accept only push notifications from websites and applications that you know and trust.
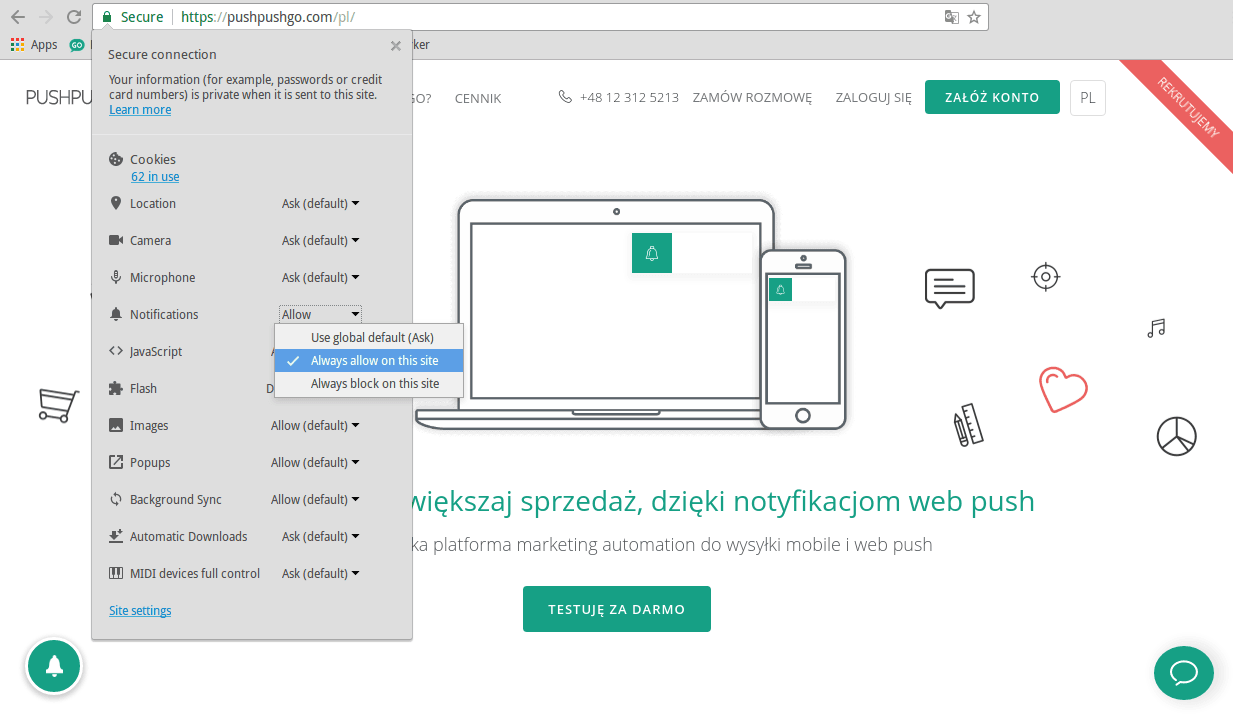
CHECK YOUR CURRENT LIST OF PUSH NOTIFICATIONS
In every web browser, you can check a list of web push notifications that you’ve accepted in the past. In Google Chrome, you have to go to the “settings” section, and then in the “privacy and security” tab, you go to the “site settings” section, where you can find the “notifications” tab. Here, you can check and manage all of your push notifications, including websites that are NOT ALLOWED to send you notifications. Check this list from time to time.
REPORT MALICIOUS WEBSITES
Both Google and Microsoft enable users to report websites containing malicious software. We encourage you to do that, too! We can all contribute to a safer, better web. All you have to do is go to a specific website, provide a link that you think is malicious or dangerous, add a short description and click the “submit” button. This way, other Internet users who encounter the same link will be warned that it’s potentially dangerous. Here are the links for you:
Report a malicious website to Google
Report a malicious website to Microsoft
Summary
Unfortunately, there is no one universal way to keep you 100% safe online. But you can easily avoid almost all the dangers out there if you act safely and think before you click any suspicious button or link. Also, don’t forget about standard forms of online protection – using reliable antivirus software and visiting only safe websites and applications. Keep all that in mind; this knowledge can help you stay safe and protect both your devices and your data online!

Content Specialist @PushPushGo
Editor and writer. She is interested in media and new technologies.
Try PushPushGo to engage and connect with your audience.
Create an account and start testing!



-o5bl3ybui6.webp)
